Sumo Logic App for AWS Network Firewall

The AWS Network Firewall application provides visibility into traffic flows and alerts generated by AWS Network Firewall.
Our new app install flow is now in Beta. It is only enabled for certain customers while we gather Beta customer feedback. If you can see the Add Integration button, follow the "Before you begin" section in the "Collect Logs" help page and then use the in-product instructions in Sumo Logic to set up the app.
Log Types
The AWS Network Firewall application uses logs generated by the AWS Network firewall. It leverages the Netflow and Alert logs.
Before you begin
Before you begin, you must:
- Enable logging from the AWS Network Firewall to an Amazon S3 bucket as described in the AWS Network Firewall documentation.
- Confirm that logs are being delivered to the S3 bucket.
- Grant Sumo Logic Access to the AWS S3 Bucket
Collecting Logs for AWS Network Firewall
This section has instructions for collecting logs for the Sumo Logic App for AWS Network Firewall Logs.
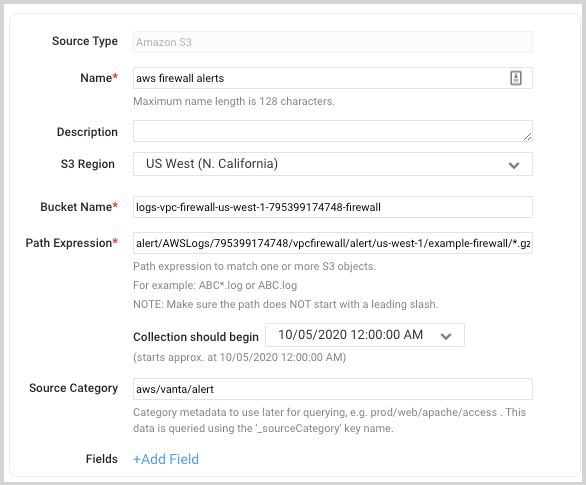
Enable S3 Ingestion
Follow steps to create AWS S3 Source.
The following is an example of a path expression that supports ingesting alerts.
Sample Log Messages
This section provides an example of AWS Network Firewall Alert and Netflow log messages.
{
"firewall_name": "example-firewall",
"availability_zone": "us-west-1b",
"event_timestamp": "1604597216",
"event": {
"timestamp": "2020-11-05T17:26:56.075365+0000",
"flow_id": 1552126922778600,
"event_type": "alert",
"src_ip": "10.0.0.227",
"src_port": 55188,
"dest_ip": "13.227.75.102",
"dest_port": 80,
"proto": "TCP",
"tx_id": 0,
"alert": {
"action": "allowed",
"signature_id": 5,
"rev": 0,
"signature": "Malicious User Agent",
"category": "",
"severity": 1
},
"http": {
"hostname": "www.somehackerurl.com",
"url": "/",
"http_user_agent": "hacker-tool-user-agent",
"http_method": "GET",
"protocol": "HTTP/1.1",
"length": 0
},
"app_proto": "http"
}
}
{
"firewall_name": "example-firewall",
"availability_zone": "us-west-1b",
"event_timestamp": "1604598416",
"event": {
"timestamp": "2020-11-05T17:46:56.003583+0000",
"flow_id": 554650891867171,
"event_type": "netflow",
"src_ip": "209.115.181.113",
"src_port": 123,
"dest_ip": "10.0.0.227",
"dest_port": 60642,
"proto": "UDP",
"app_proto": "ntp",
"netflow": {
"pkts": 1,
"bytes": 90,
"start": "2020-11-05T17:41:54.611363+0000",
"end": "2020-11-05T17:41:54.675362+0000",
"age": 0,
"min_ttl": 43,
" max_ttl": 238
}
}
}
Sample Query
This section provides a sample from the Traffic By Application panel on the AWS Network Firewall - Netflow Overview dashboard.
_sourceCategory=aws/vanta/*
| json "firewall_name", "availability_zone", "event" nodrop
| json field=event "event_type", "src_ip", "src_port", "dest_ip", "dest_port", "proto", "app_proto", "netflow" nodrop
| json field=netflow "bytes", "pkts" nodrop
| where event_type="netflow"
| timeslice 15m
| count _timeslice, app_proto
| transpose row _timeslice column app_proto
Installing the AWS Network Firewall App
This section provides instructions for installing the Sumo Logic App for AWS Network Firewall. To install the app, do the following:
Locate and install the app you need from the App Catalog. If you want to see a preview of the dashboards included with the app before installing, click Preview Dashboards.
- From the App Catalog, search for and select the app.
- Select the version of the service you're using and click Add to Library. Version selection is applicable only to a few apps currently. For more information, see the Install the Apps from the Library..
- To install the app, complete the following fields.
- App Name. You can retain the existing name, or enter a name of your choice for the app.
- Data Source. Select either of these options for the data source.
- Choose Source Category, and select a source category from the list.
- Choose Enter a Custom Data Filter, and enter a custom source category beginning with an underscore. Example: (
_sourceCategory=MyCategory).
- Advanced. Select the Location in Library (the default is the Personal folder in the library), or click New Folder to add a new folder.
- Click Add to Library.
Once an app is installed, it will appear in your Personal folder, or other folder that you specified. From here, you can share it with your organization.
Panels will start to fill automatically. It's important to note that each panel slowly fills with data matching the time range query and received since the panel was created. Results won't immediately be available, but with a bit of time, you'll see full graphs and maps.
Viewing AWS Network Firewall Dashboards
This section offers descriptions and examples for each of the pre-configured app dashboards.
Template variables provide dynamic dashboards that can rescope data on the fly. As you apply variables to troubleshoot through your dashboard, you view dynamic changes to the data for a quicker resolution to the root cause. You can use template variables to drill down and examine the data on a granular level. For more information, see Filter with template variables.
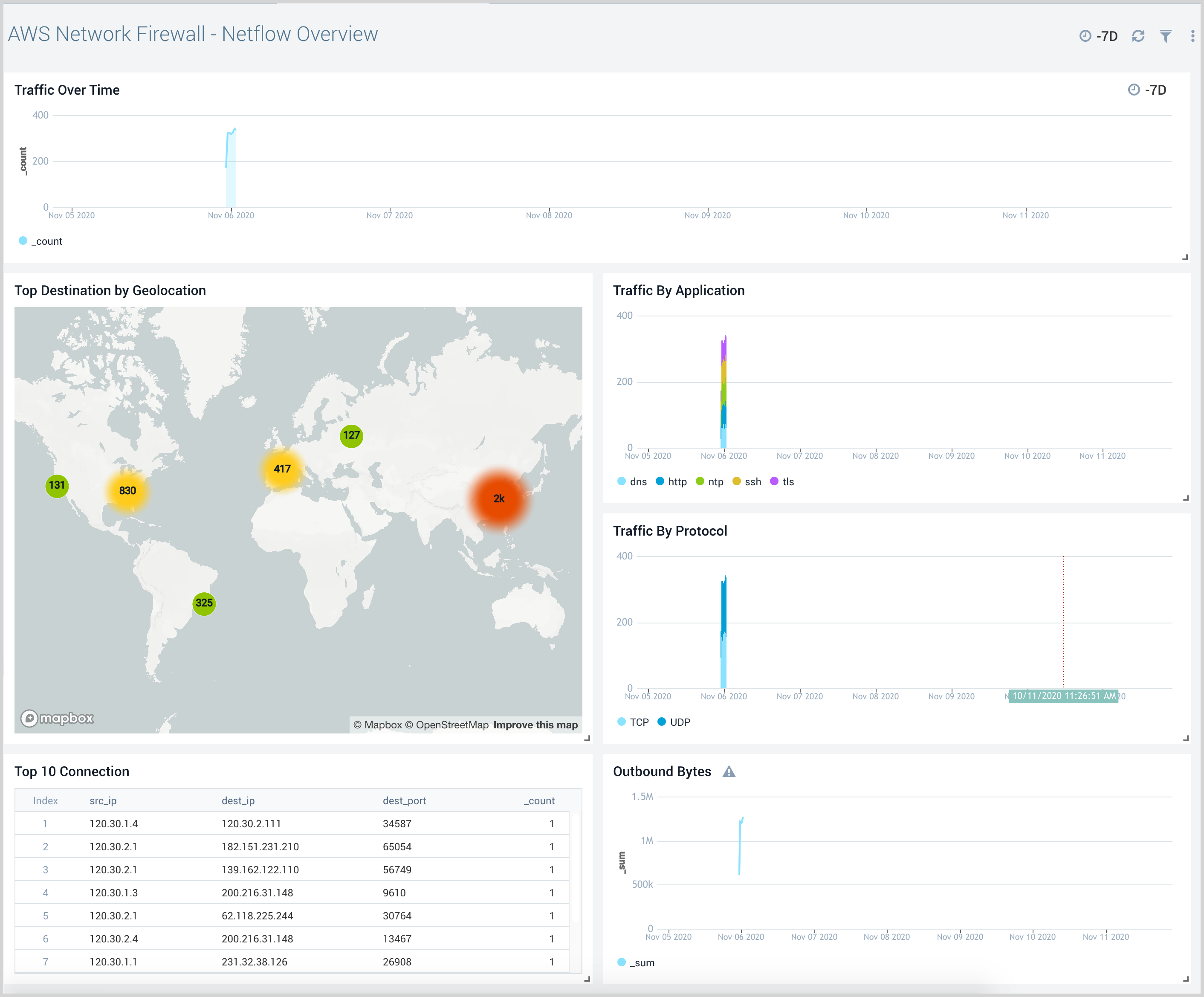
Netflow Overview
The AWS Network Firewall - Netflow Overview provides visibility into network flows traversing across the firewall. This includes visibility into traffic by application, protocol, traffic over time, and top connections.
Use this dashboard to:
- Monitor traffic types and rates traveling through the firewall
- Gain visibility into common protocols and hosts in use behind the firewall.
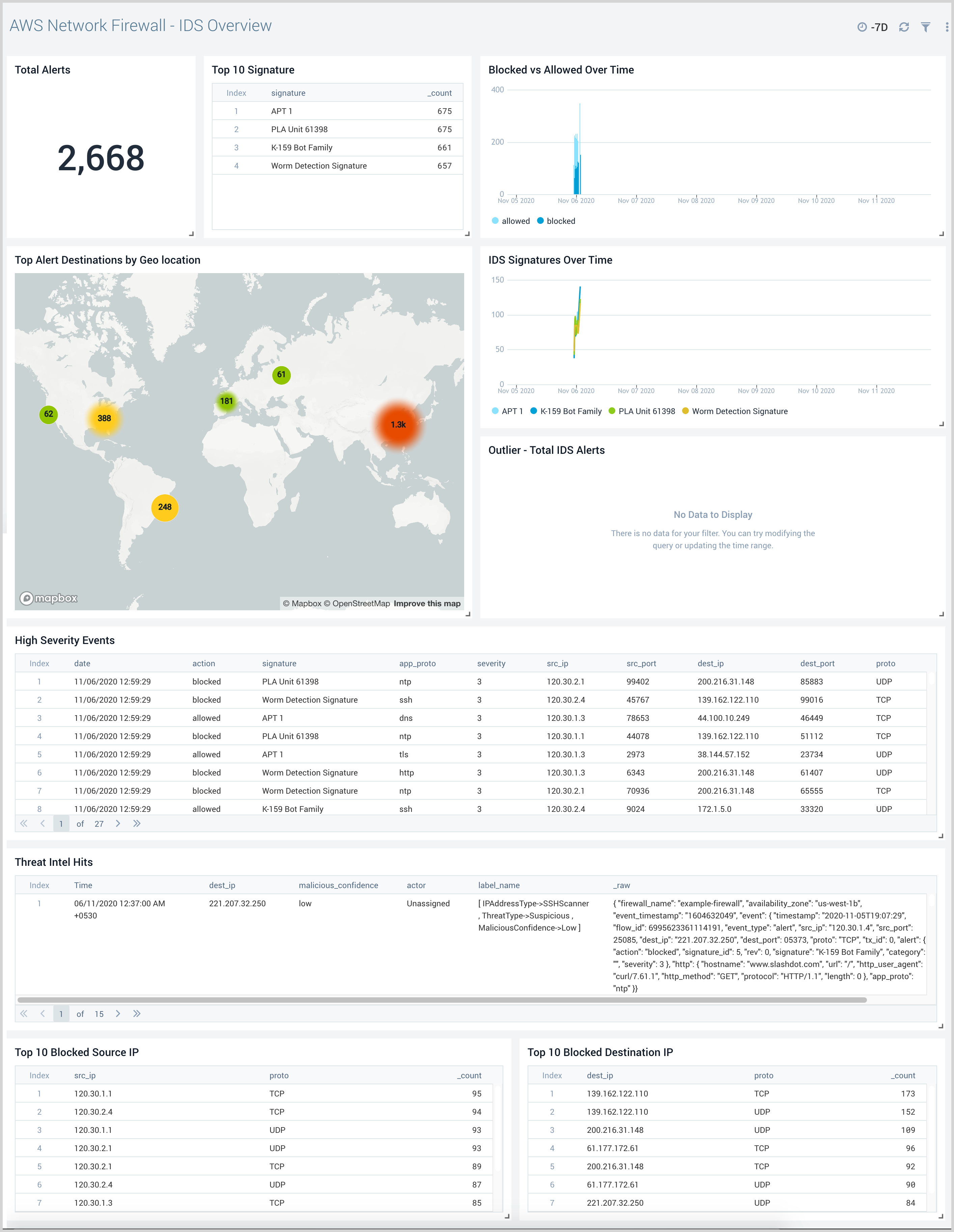
IDS Overview
The AWS Network Firewall - IDS Overview provides visibility into alerts generated by the firewall rules. This includes geolocation information on top destinations, alerts over time, correlation with CrowdStrike threat intelligence data, and top systems blocked.
Use this dashboard to:
- Gain visibility into alerts generated by the AWS Network Firewall including location information from top destinations.
- Gain visibility into traffic from malicious IPs determined by correlating AWS Network Firewall data with Crowdstrike Threat Intelligence data.