AWS CloudTrail Source

AWS CloudTrail records API calls made to AWS. This includes calls made using the AWS Management Console, AWS SDKs, command line tools, and higher-level AWS services. Add an AWS CloudTrail Source to upload these messages to Sumo Logic. The AWS CloudTrail Source automatically parses the logs prior to upload.
You need to know where your CloudTrail log files are stored so you can provide the path to the AWS CloudTrail Source. Refer to AWS Documentation for finding your CloudTrail log files.
Tutorial: Set up an AWS CloudTrail Source.
Configure an AWS CloudTrail Source
- Configure CloudTrail in your AWS account. This will create an S3 bucket for you if you so choose.
- Grant Sumo Logic access to an Amazon S3 bucket created or used above.
- Confirm that logs are being delivered to the Amazon S3 bucket.
- In Sumo Logic select Manage Data > Collection > Collection.
- Select the hosted Collector for which you want to add the Source, and click Add Source. To create a new hosted collector, see Configure a Hosted Collector.
- Select AWS CloudTrail.
- The page refreshes.
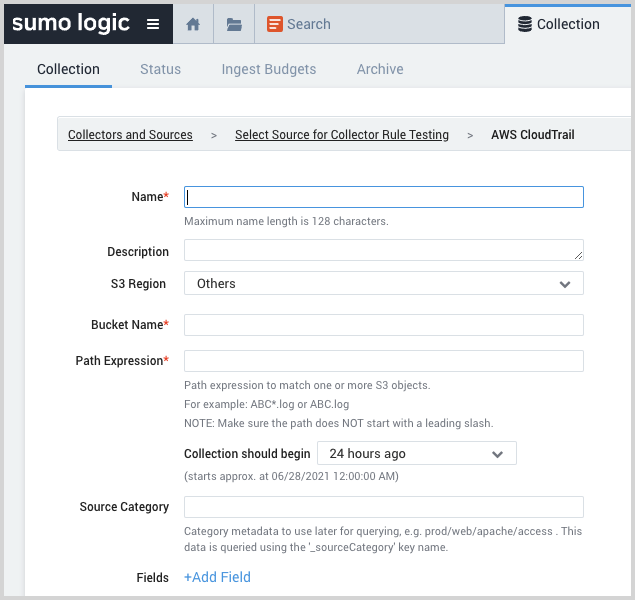
- Name. Enter a name for the source.
- Description. (Optional)
- S3 Region. Choose the AWS Region the S3 bucket resides in.
- Bucket Name. The name of your organizations S3 bucket as it appears in AWS.
- Path Expression. The path expression of the log file(s) in S3, can contain wildcards to include multiple log files.
- Source Category. Enter a string to tag the output collected from the source. The string that you supply will be saved in a metadata field called
_sourceCategory. - AWS Access. For AWS Access you have two Access Method options. Select Role-based access or Key access based on the AWS authentication you are providing. Role-based access is preferred. Note that Sumo Logic access to AWS (instructions are provided above in Step 1) is a prerequisite for role-based access
- Role-based access. Enter the Role ARN that was provided by AWS after creating the role.
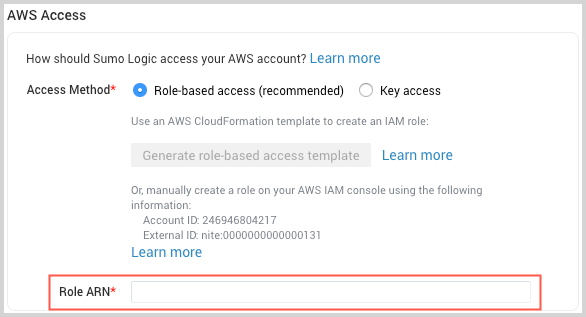
- Key access. Enter the Access Key ID and Secret Access Key. See AWS Access Key ID and AWS Secret Access Key for details.
- Role-based access. Enter the Role ARN that was provided by AWS after creating the role.
- Click SAVE.
- Optional: Install the Sumo Logic App for AWS CloudTrail.
CloudTrail log objects
CloudTrail log objects are generated by AWS as a single JSON Records array containing a series of event objects. The AWS CloudTrail Source automatically applies boundary and timestamp processing rules to pull the individual event objects from the CloudTrail Records array as separate log messages within Sumo Logic.
The following is an example of an AWS CloudTrail file object:
{"Records":[{"eventVersion":"1.03","userIdentity":{"type":"Root","principalId":"XXXXXXXXXX","arn":
"arn:aws:iam::XXXXXXXXXX:root","accountId":"XXXXXXXXXX","accessKeyId": "XXXXXXXXXXXXXXXX","sessionContext":
{"attributes":{"mfaAuthenticated":"false", "creationDate":"2016-04-01T16:09:43Z"}}}, "eventTime":
"2016-04-01T16:19:26Z","eventSource":"s3.amazonaws.com","eventName":"GetBucketLocation","awsRegion":
"us-west-2","sourceIPAddress":" 192.168.1.1","userAgent":"[S3Console/0.4]","requestParameters":
{"bucketName":"example"},"responseElements":null,"requestID":"DE61373E09329981","eventID":
"d4877d6c-4bf2-4a46-82d5-c8d710905138","eventType":"AwsApiCall","recipientAccountId":"XXXXXXXXXX"},
{"eventVersion": "1.03","userIdentity":"type":"Root","principalId":"XXXXXXXXXX","arn":
"arn:aws:iam::XXXXXXXXXX:root","accountId": "XXXXXXXXXX","accessKeyId":"XXXXXXXXXXXXXXXX","sessionContext":
{"attributes":{"mfaAuthenticated":"false", "creationDate":"2016-04-01T16:09:43Z"}}},"eventTime":
"2016-04-01T16:19:26Z","eventSource":"s3.amazonaws.com", "eventName":"GetBucketLocation","awsRegion":
"us-west-2","sourceIPAddress":" 192.168.1.1","userAgent": "[S3Console/0.4]","requestParameters":
{"bucketName":"example"},"responseElements":null,"requestID": "F1A6B08803D73C5A","eventID":
"2b4d6eea-ecb8-4853-a1d2-f0b6b931d5bf","eventType":"AwsApiCall","recipientAccountId":
"XXXXXXXXXX"}, {"eventVersion":"1.04","userIdentity":"type":"Root","principalId":"XXXXXXXXXX","arn":
"arn:aws:iam::XXXXXXXXXX:root","accountId":"XXXXXXXXXX","accessKeyId":"XXXXXXXXXXXXXXXX","sessionContext":
{"attributes":{"mfaAuthenticated":"false","creationDate":"2016-04-01T16:09:43Z"}}},"eventTime":
"2016-04-01T16:22:11Z","eventSource":"cloudtrail.amazonaws.com","eventName":"DescribeTrails","awsRegion":
"us-west-2","sourceIPAddress":"10.1.1.1","userAgent":"console.amazonaws.com","requestParameters":
{"trailNameList":[]},"responseElements":null,"requestID":"e36e19ff-f825-11e5-9015-0336c0231e57", "eventID":
"9b5a6b39-0415-4c88-b7f1-698161bf028b","eventType":"AwsApiCall","recipientAccountId":
"XXXXXXXXXX"},{"eventVersion": "1.04","userIdentity":"type":"Root","principalId":"XXXXXXXXXX",
"arn":"arn:aws:iam::XXXXXXXXXX:root","accountId": "XXXXXXXXXX","accessKeyId":"XXXXXXXXXXXXXXXX",
"sessionContext":{"attributes":{"mfaAuthenticated":"false", "creationDate":"2016-04-01T16:09:43Z"}}},
"eventTime":"2016-04-01T16:22:34Z","eventSource":"cloudtrail.amazonaws.com", "eventName":"DescribeTrails",
"awsRegion":"us-west-2","sourceIPAddress":"10.1.1.1","userAgent":"console.amazonaws.com", "requestParameters":
{"trailNameList":[]},"responseElements":null,"requestID": "f0c79c48-f825-11e5-933d-65f8283355b7", "eventID":
"2f9837ef-f727-45d7-a217-2974d27cb998","eventType": "AwsApiCall","recipientAccountId":"XXXXXXXXXX"}}
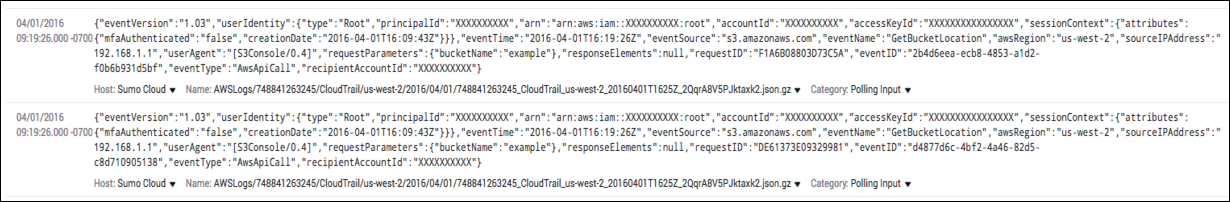
CloudTrail events as seen in Sumo Logic:
AWS Sources
See AWS Sources for more information.