CSE Audit Logging
The Audit Event Index provides event logs in JSON format on your account activity so you to monitor and audit changes. By default the Audit Event Index is enabled for CSE and Enterprise accounts.
This page describes functionality that is available to users whose CSE URL ends in sumologic.com.
Where to find the documentation
The audit logging documentation is hosted on each Sumo Logic deployment. Sumo Logic has several deployments that are assigned depending on the geographic location and the date an account is created. If you're not sure what what your deployment is, see how to determine which endpoint to use.
Select the documentation link for your deployment:
| Deployment | Location | Documentation URL |
|---|---|---|
| AU | Australia | https://service.au.sumologic.com/audit/docs/sec |
| JP | Japan | https://service.jp.sumologic.com/audit/docs/sec |
| IN | India | https://service.in.sumologic.com/audit/docs/sec |
| US1 | United States | https://service.sumologic.com/audit/docs/sec |
| US2 | United States | https://service.us2.sumologic.com/audit/docs/sec |
Scoping your Audit Index search
This section explains how to scope a search of the Audit Event Index to return CSE events.
Limit search to user or system events
CSE audit events are stored in two Partitions:
sumologic_audit_events. This index contains user action events, which are events that were triggered by a user action, either from the UI or an API. For example, a user created an Insight from a Signal using the CSE UI.sumologic_system_events. This index contains system action events, which are events that were triggered by the system. For example, an Insight was generated by CSE.
Use _index=sumologic_audit_events to limit results to events related to user actions
Use _index=sumologic_system_events to limit results to events related to system actions.
Limit search to CSE events
You can use the subsystem field, which every event log contains, to limit the events returned to CSE-related events:
subsystem=cse
For information about other fields you can use in Audit Index searches, see auto-generated documentation at the documentation URL for your deployment.
Limit search by CSE feature
The table below shows the _sourceCategory that is assigned to event logs by CSE feature.
| Product Feature | _sourceCategory Value |
|---|---|
| Action | cseAction |
| Aggregation Rule | cseRule |
| Configure Assigned Insight Emails (Relates to the option, on the Actions page, that causes a user to receive an email whenever another user assigns an Insight to them. | cseConfiguration |
| Chain Rule | cseRule |
| Cloud SOAR Incident | cseCloudSoar |
| Context Action | cseContextAction |
| Custom Entity Type | cseCustomEntityType |
| Custom Insight | cseCustomInsight |
| Custom Match List Column | cseCustomMatchListColumn |
| Custom Tag Schema | cseCustomTagSchema |
| Customer Sourced Entity Lookup Table | cseCustomerSourcedEntityLookupTable |
| Entity | cseEntity |
| Entity Criticality Config | cseEntityCriticalityConfig |
| Entity Domain Configuration | cseEntityNormalization |
| Favorite Field | cseFavoriteField |
| Insight | cseInsight |
| Inventory Entity Lookup Table | cseInventoryEntityLookupTable |
| Log Mapping | cseLogMapping |
| Match List | cseMatchList |
| Match Rule | cseRule |
| Network Block | cseNetworkBlock |
| Streaming Export Configuration | cseStreamingExportConfiguration |
| Sumo Mapping | cseSumoMapping |
| Suppressed List | cseSuppressList |
| Templated Match Rule | cseRule |
| Threat Intel Sources (Applies to all source types on the Threat Intel page.) | cseThreatIntelSource |
| Threshold Rule | cseRule |
| Virus Total Configuration | cseConfiguration |
| Yara Rule | cseYara |
| Yara Source | cseYara |
_sourceName and _sourceHost assignment
The _sourceName and _sourceHost fields are assigned to audit event
logs as follows.
| Metadata Field | Assignment Description |
|---|---|
_sourceName | Value of the common parameter, eventName. |
_sourceHost | The remote IP address of the host that made the request. If not available the value will be no_sourceHost. |
Common parameters
Each audit event log has common keys that categorize it to a product area and provide details of the event.
| Parameter | Description | Data Type |
|---|---|---|
accountId | The unique identifier of the organization. | String |
eventId | The unique identifier of the event. | String |
eventName | The name of the event. | String |
eventTime | The event timestamp in ISO 8601 format. | String |
eventFormatVersion | The event log format version. | String |
operator | Information of who did the operation. If its missing, the Sumo service was the operator. | JSON object of Strings |
subsystem | The product area of the event. | String |
Search the Audit Event Index
To search the Audit Event Index for logs that describe CSE events:
- Open a search tab in the Sumo Logic UI by clicking + New and choosing Log Search.
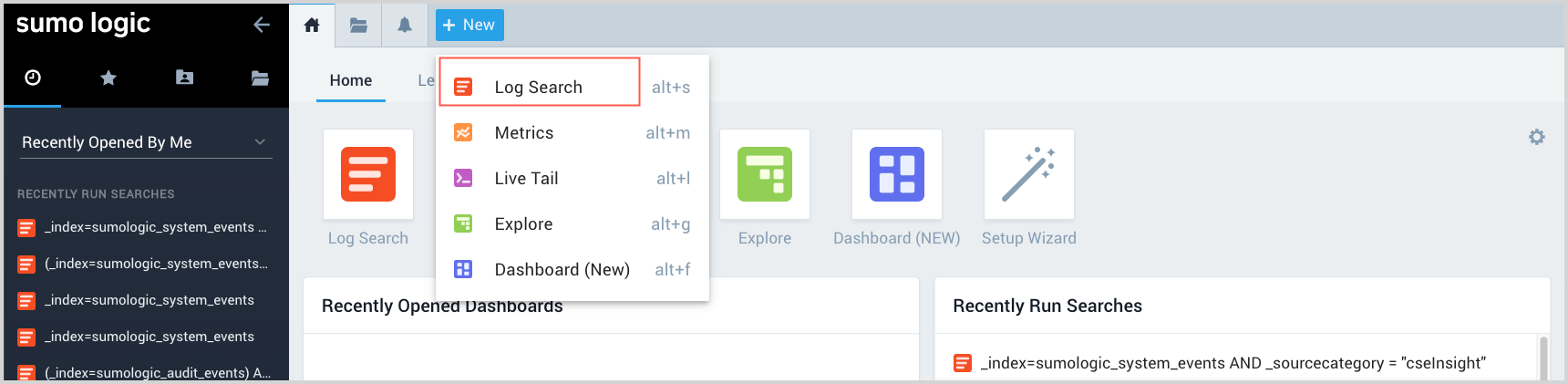
- In the search tab, enter a search using
_indexto specify the partition you want to search, other metadata or fields to further scope you search. For example:_index=sumologic_system_events
| json auto
| where subsystem="cse" - Choose the time range for your search.
- Click Start to run the search.
Example event log
Here is an example InsightCreated event log.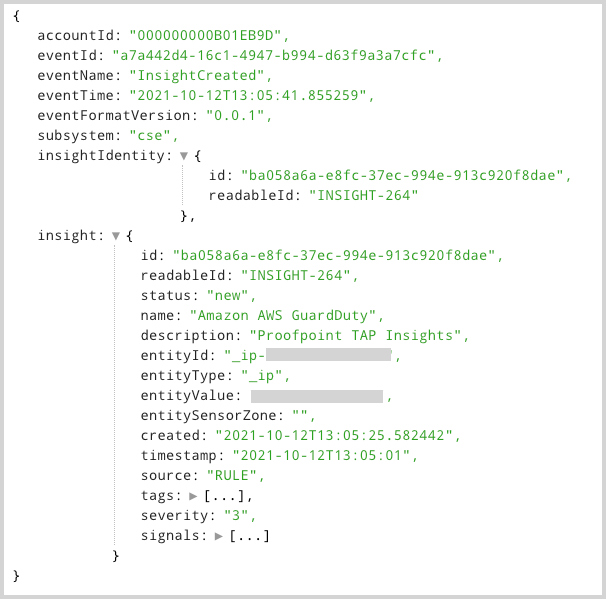
Index retention period
By default, the retention period of the Audit Event Index is the same as the retention period of your Default Partition. You can change the retention period by editing the relevant partitions, sumologic_audit_events and sumologic_system_events. For more information, see Edit a Partition.

