Collect Logs from Azure Blob Storage
This section has instructions for configuring a pipeline for shipping logs available from Azure Blob Storage to an Event Hub, on to an Azure Function, and finally to an HTTP source on an hosted collector in Sumo Logic.
Requirements
- Only General-purpose v2 (GPv2) and Blob storage accounts are supported. This integration does not support General-purpose v1 (GPv1) accounts.
- Configure your storage account in the same location as your Azure Service.
- This solution supports only log files from Blob storage that have file extensions of .csv, .json, .blob, or .log.
- You also need to have Microsoft Authorization/role Assignments/write permissions, so they should be a "User Access Administrator" or "Owner".
Functional overview
- You configure the Azure service to export logs to a container in a storage account created for that purpose.
- The ARM template creates an Event Grid subscription with the storage container as publisher and the event hub (created by the Sumo-provided ARM) as subscriber. Event Grid routes block blob creation events to event hub.
- Event Hub streams the events to the TaskProducer Azure function, which creates tasks (a JSON object that specifies start and end byte, container name, blob path) and pushes those tasks to the service bus task queue.
- The TaskConsumer Azure function, which is triggered when the service bus receives a new task, reads the block blob, from start byte to stop byte, and sends that data to Sumo.
- The set up also includes failure handling mechanism. For more information about the solution strategy, see Azure Blob Storage.
Step 1. Configure Azure storage account
In this step you configure a storage account to which you will export monitoring data for your Azure service.
The storage account must be a General-purpose v2 (GPv2) storage account
If you have a storage account with a container that you want to use for this purpose, make a note of its resource group, storage account name and container name and proceed to Step 2.
To configure an Azure storage account, do the following:
Create a new storage account General-purpose v2 (GPv2) storage account. For instructions, see Create a storage account in Azure help.
Create a container(Optional) all services in azure create containers automatically. This step is needed only when you are exporting custom logs in some container.
- In the Azure portal, navigate to the storage account you just created (in the previous step).
- Select Blobs under Blob Service.
- Select + Container.
- Enter the Name.
- Select Private for the Public Access Level.
- Click OK.
Make a note of the container name, you will need to supply it later.
Step 2. Configure an HTTP source
In this step, you configure an HTTP source to receive logs from the Azure function.
- Select a hosted collector where you want to configure the HTTP source. If desired, create a new hosted collector, as described on Configure a Hosted Collector.
- Configure an HTTP source, as described on HTTP Logs and Metrics Source. Make a note of the URL for the source, you will need it in the next step.
Step 3. Configure Azure resources using ARM template
In this step, you use a Sumo-provided Azure Resource Manager (ARM) template to create an Event Hub, three Azure functions, Service Bus Queue, and a Storage Account.
Download the blobreaderdeploy.json ARM template.
noteThe above template uses Consumption Plan which does not support VNet integration, you can use blobreaderdeploywithPremiumPlan.json which uses Elastic Premium plan.
Click Create a Resource, search for Template deployment in the Azure Portal, and then click Create.
On the Custom deployment blade, click Build your own template in the editor.
Copy the contents of the template and paste it into the editor window.
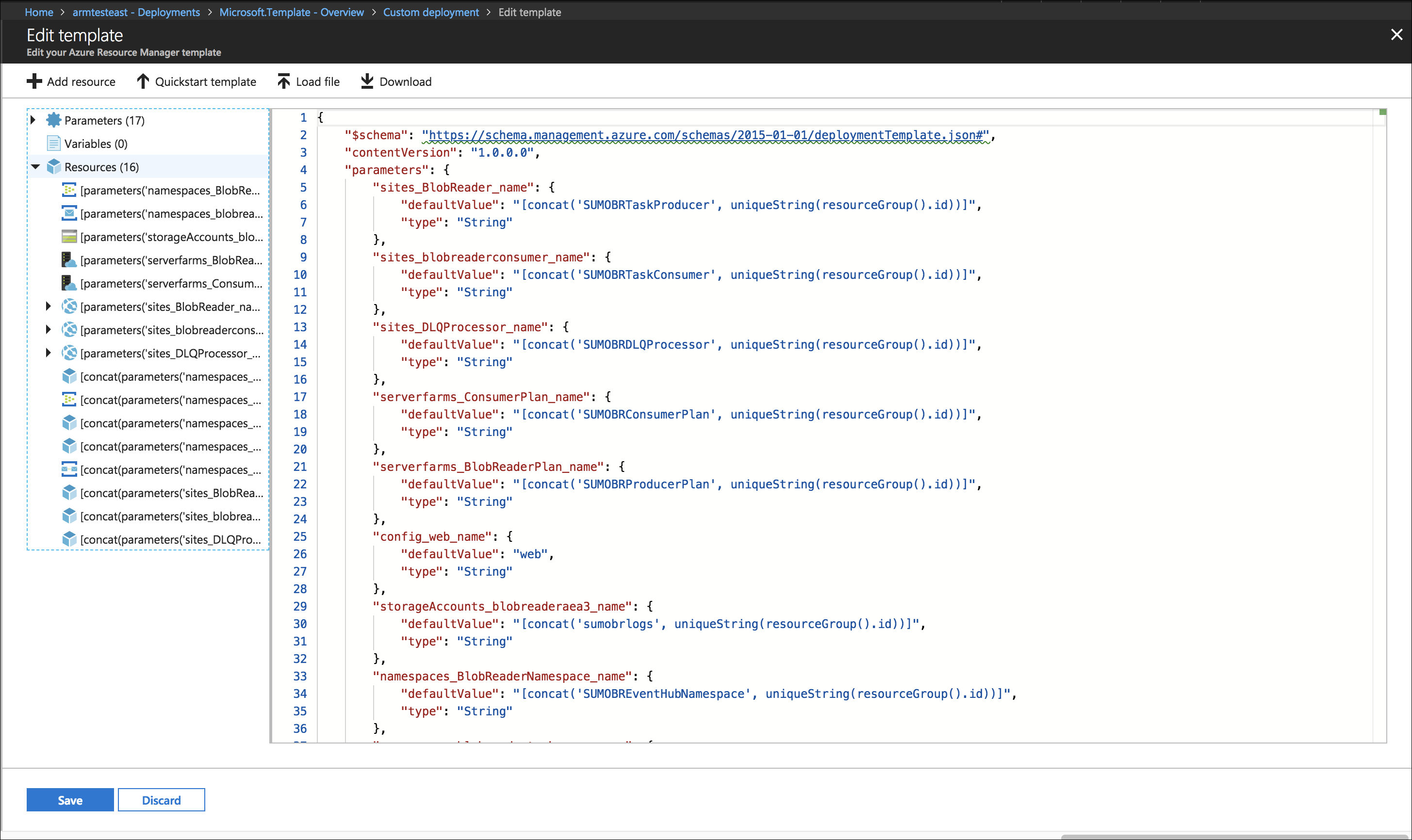
Click Save.
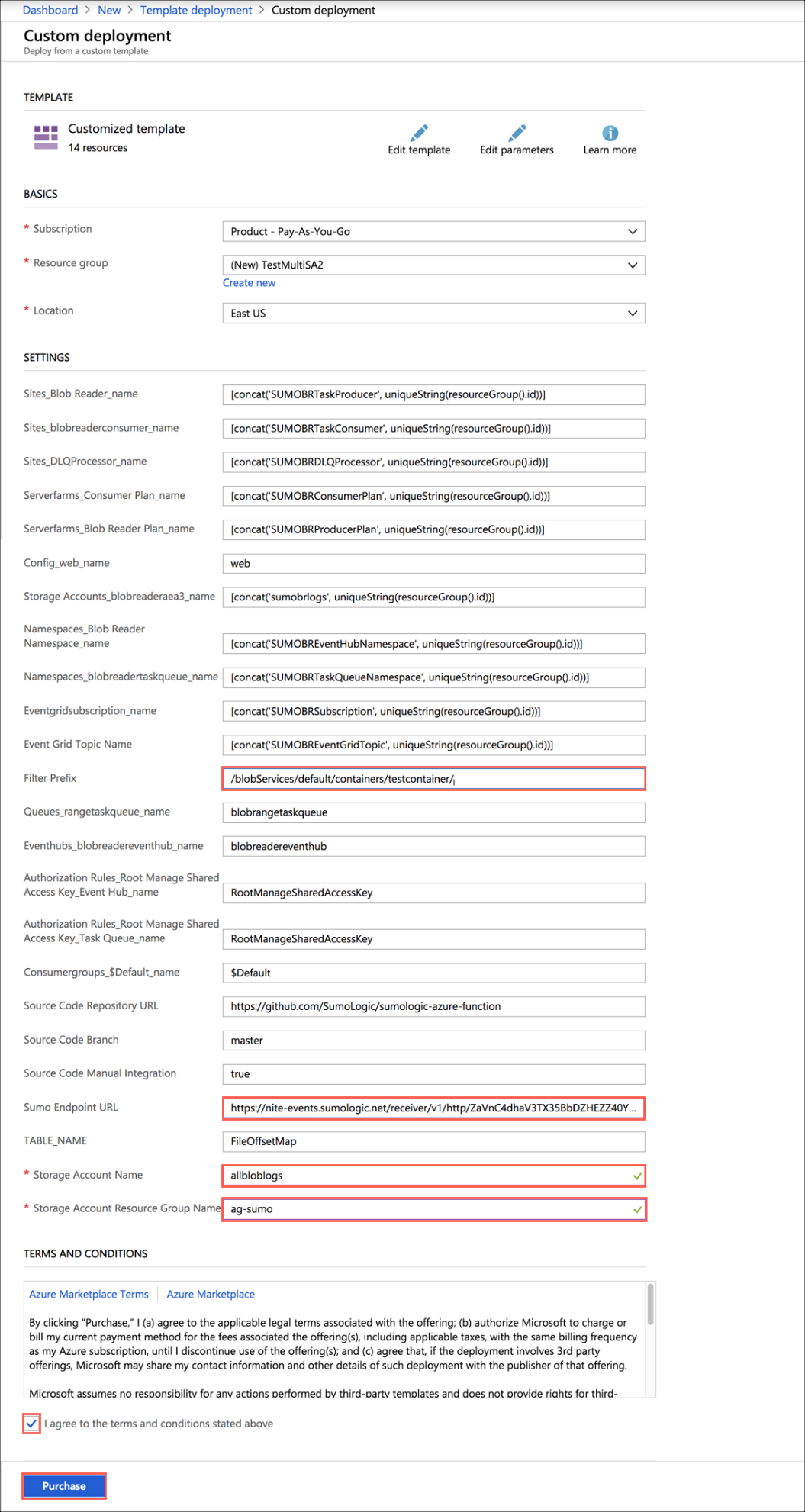
On the Custom deployment blade, do the following:
Create a new Resource Group (recommended) or select an existing one.
Choose Location.
Set the values of the following parameters:
- SumoEndpointURL: URL for the HTTP source you configured in Step 2 above.
- StorageAccountName: Name of the storage account where you are storing logs from Azure Service, that you configured in Step 1 above.
- StorageAccountResourceGroupName: Name of the resource group of the storage account you configured in Step 1 above.
- Filter Prefix (Optional): If you want to filter logs from a specific container, enter the following, replacing the variable with your container name:
/blobServices/default/containers/<container_name>/
noteResource group names should not consist of an underscore.
Select the check box to agree to the terms and conditions, and then click Purchase.
Verify the deployment was successful by looking at Notifications at top right corner of Azure Portal.
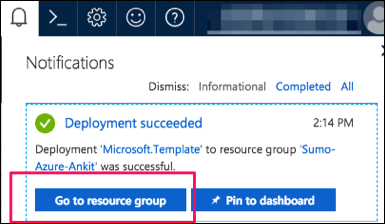
(Optional) In the same window, click Go to resource group to verify the all resources were successfully created, such as shown in the following example:
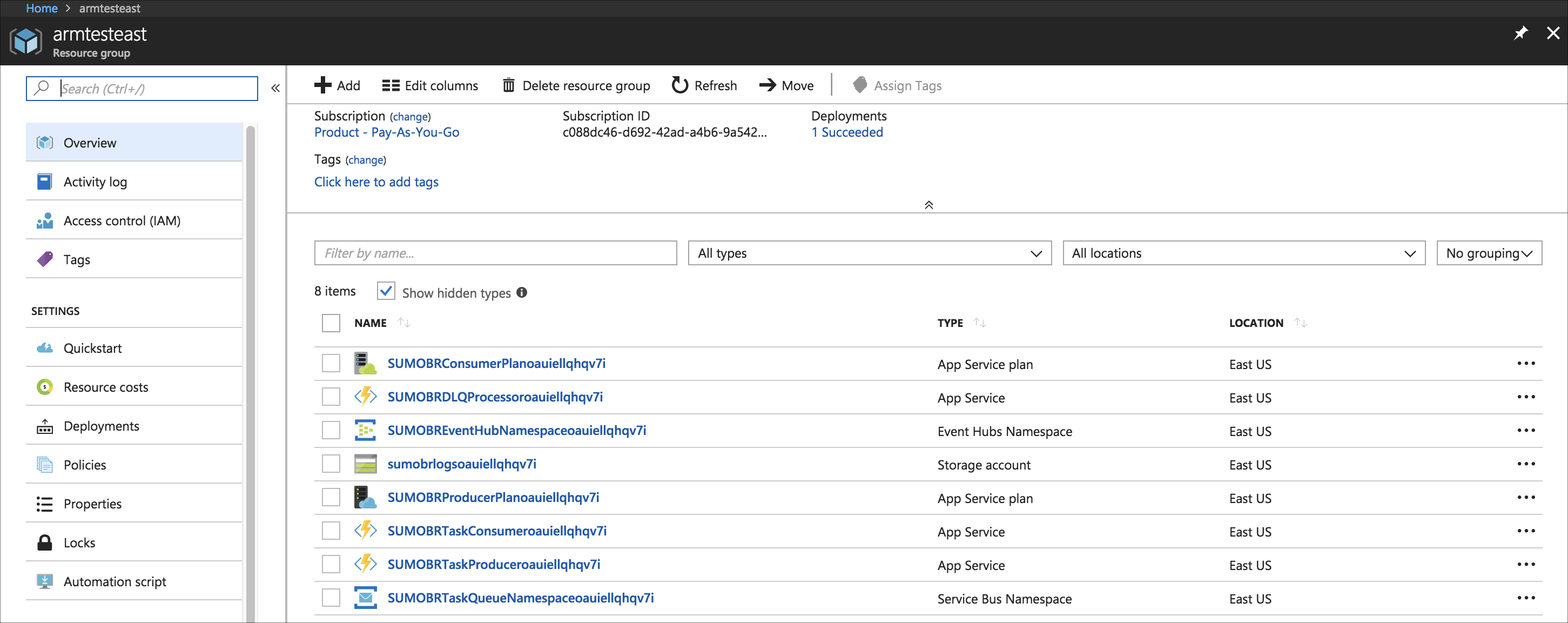
Go to Storage accounts and search for sumobrlogs, then select sumobrlogs\<random-string\>.
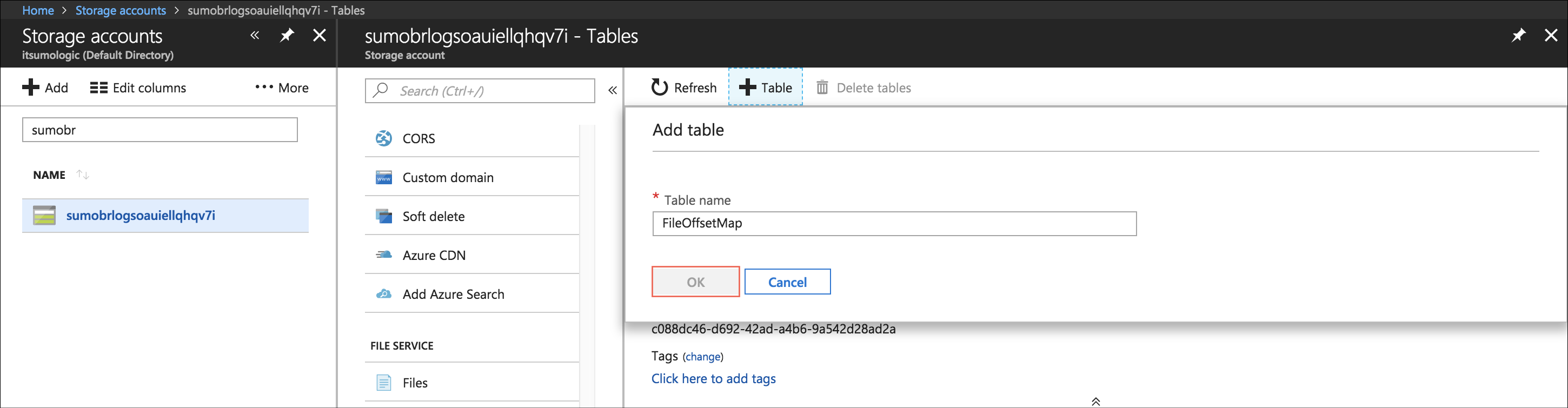
Under Table Service do the following:
- Click Tables.
- Click + Table.
- For Name, enter FileOffsetMap.
Click OK.
Step 4. Push logs from Azure Service to Azure Blob Storage
This section describes how to push logs from an Azure service to Azure Blob Storage by configuring Diagnostic Logs. The instructions use the Azure Web Apps Service as an example.
Login to the Azure Portal.
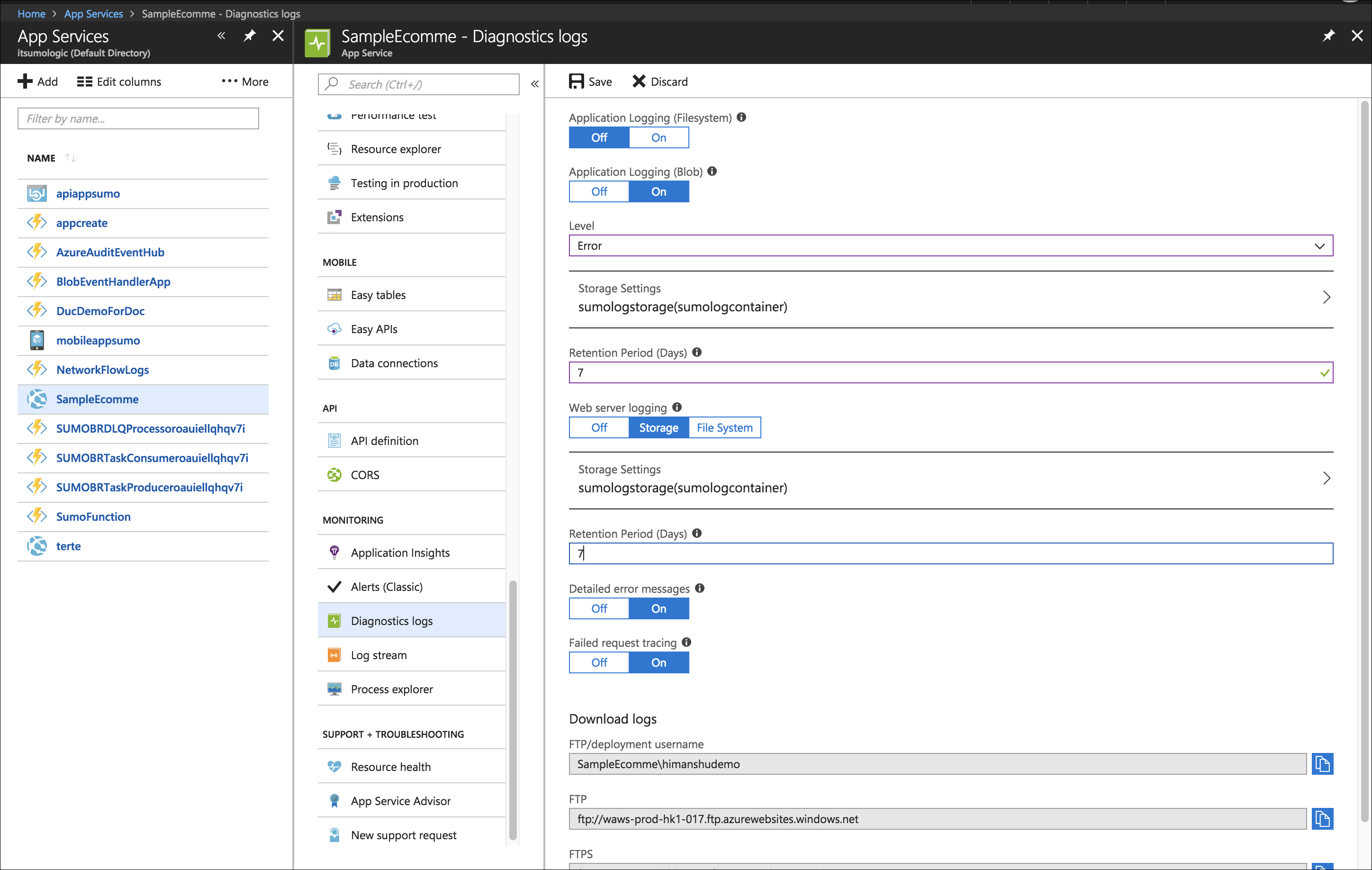
Click AppServices > Your Function App > Diagnostic Logs under Monitoring.
You will see the Diagnostic Logs blade. Enable Application Logging, Web Server Logging, or both, and click Storage Settings.
Select the Storage Account whose connection string you configured in Step 1.
In the Containers blade, select the container you created in Step 1.
In the Diagnostic Logs blade, specify the Retention Period (Days), and click Save to exit Diagnostic Logs configuration.
If logs from Azure Blob Storage do not start to flow into Sumo, see Troubleshoot Azure Blob Storage Log Collection.
Ingesting from Multiple Storage Accounts (Optional)
If you want to ingest data into Sumo from multiple storage accounts, perform following tasks for each storage account separately.
The following steps assume you have noted down the resource group name, storage account name, and container name where the blobs will be ingested from.
- Step 1: Authorize App Service to list storage Account key - Enables the Azure functions to read from the storage account.
- Step 2: Create an Event Grid Subscription - Subscribes all blob creation events to the Event Hub created by ARM template in Step 3 above.
- Step 3. Enabling Vnet Integration(Optional)
Step 1: Authorize App Service to list Storage Account key
This section provides instructions on authorizing the App Service to list the Storage Account key. This enables the Azure function to read from the storage account.
To authorize the App Service to list the Storage Account key, do the following:
Go to Storage Account and click Access Control(IAM).
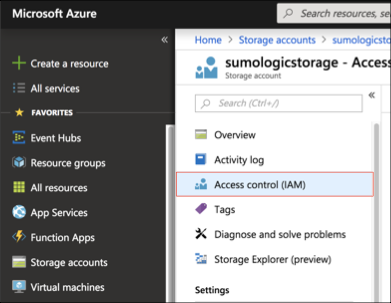
Click the Add + at the top of the page.
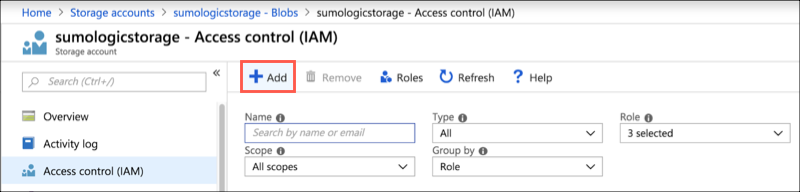
Select Add role assignment from dropdown.
In the Add role Assignment window, go to Roles tab and Choose “Storage Account Key Operator Service Role”. Click Next.
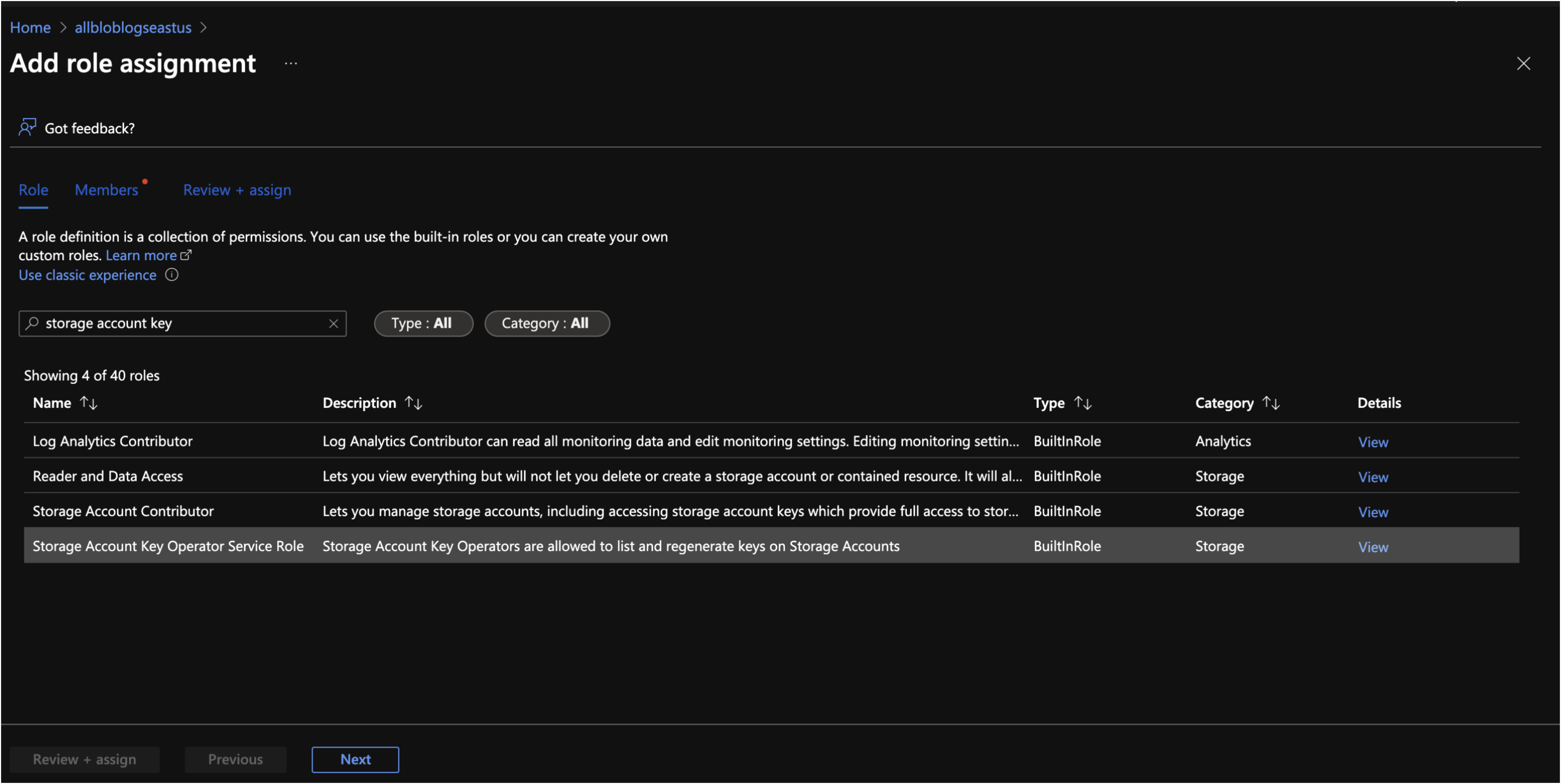
In Members tab, select Managed Identity.
In the Select Managed identities window.
Subscription: Choose Pay as you Go
Managed Identity: Choose Function App
Select: Select SUMOBRDLQProcessor\<unique_prefix> and SUMORTaskConsumer\<unique_prefix> app services which are created by the ARM template. Click Select.

Click Review + assign
Click Save.
Step 2: Create an Event Grid Subscription
This section provides instructions for creating an event grid subscription, that subscribes all blob creation events to the Event Hub created by ARM template in Step 3 above.
To create an event grid subscription, do the following:
In the left pane of Azure portal click All Services, then search for and click Event Grid Subscriptions.
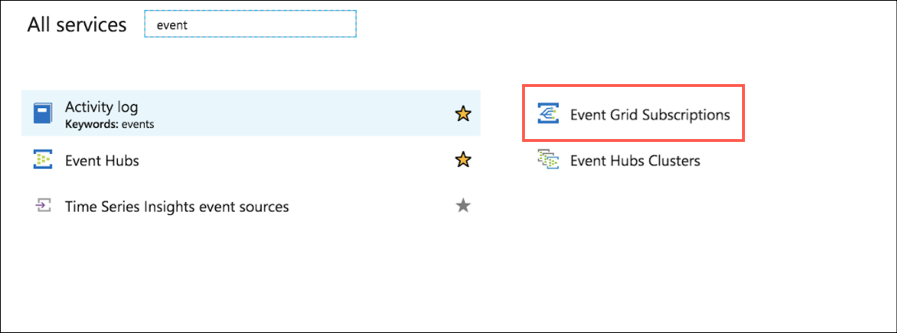
At the top of the Event subscriptions page, click +Event Subscription.
The Create Event Subscription dialog appears.
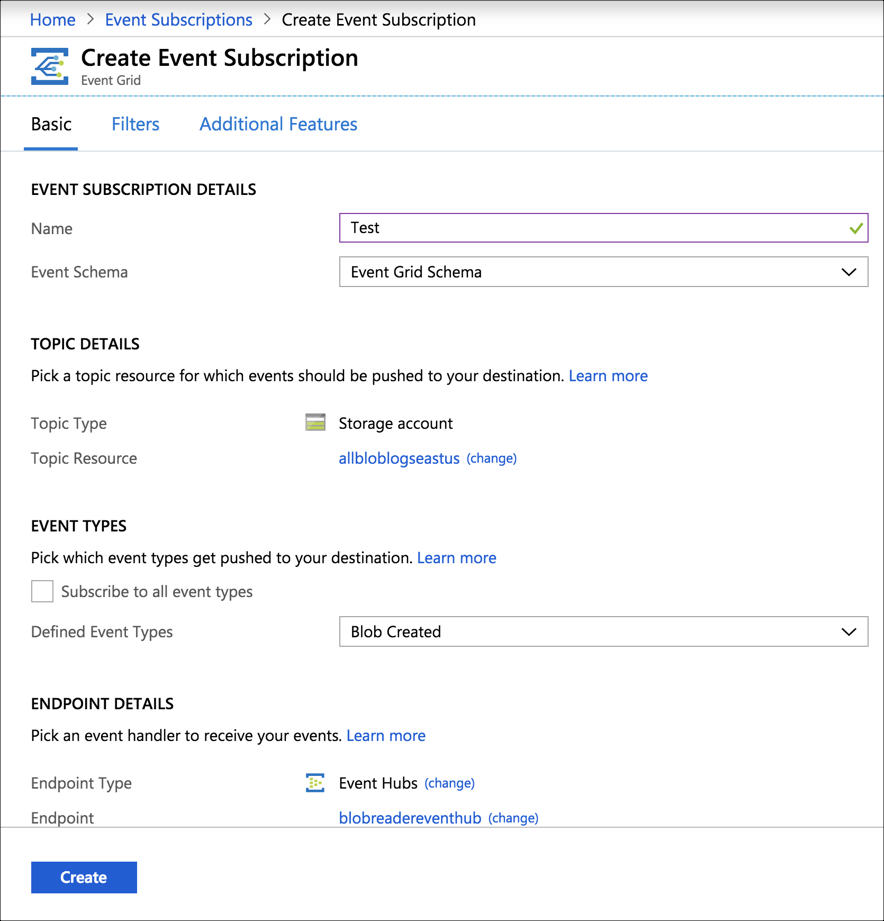
Specify the following values for Event Subscription Details:
- Name: Fill the event subscription name.
- Event Schema: Select Event Grid Schema.
Specify the following values for Topic Details:
Topic Type. Select Storage Accounts.
Subscription. Select Pay As You Go
Resource Group. Select the Resource Group for the Storage Account to which your Azure service will export logs, from where you want to ingest logs.
Resource. Select the Storage Account you configured, from where you want to ingest logs.
noteIf you don't see your configured Storage Account in the dropdown menu, make sure you met the requirements in Requirements section.
Specify the following details for Event Types:
- Uncheck the Subscribe to all event types box.
- Select Blob Created from the Define Event Types dropdown.
Specify the following details for Endpoint Types:
Endpoint Type. Select Event Hubs from the dropdown.
Endpoint. Click on Select an endpoint.
The Select Event Hub dialog appears.
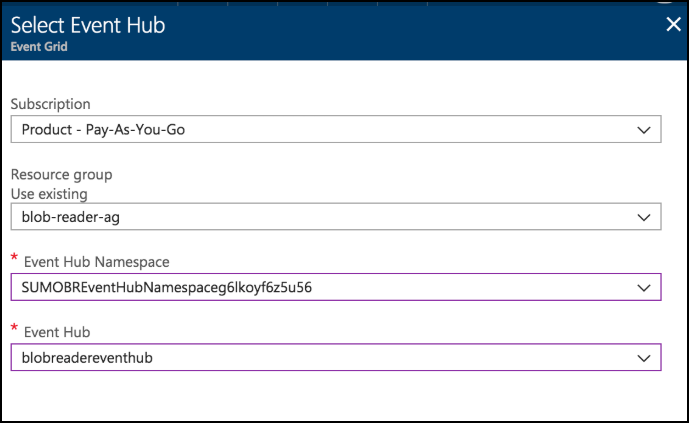
Specify the following Select Event Hub parameters, then click Confirm Selection.
- Resource Group. Select the resource group you created Step 3 in which all the resources created by ARM template are present.
- Event Hub Namespace. Select SUMOBREventHubNamespace\<unique string\>.
- Event Hub. Select blobreadereventhub from the dropdown.
Specify the following Filters tab options:
- Check Enable subject filtering.
- To filter events by container name, enter the following in the Subject Begins With field, replacing
<container_name>with the name of the container from where you want to export logs./blobServices/default/containers/<container_name>/
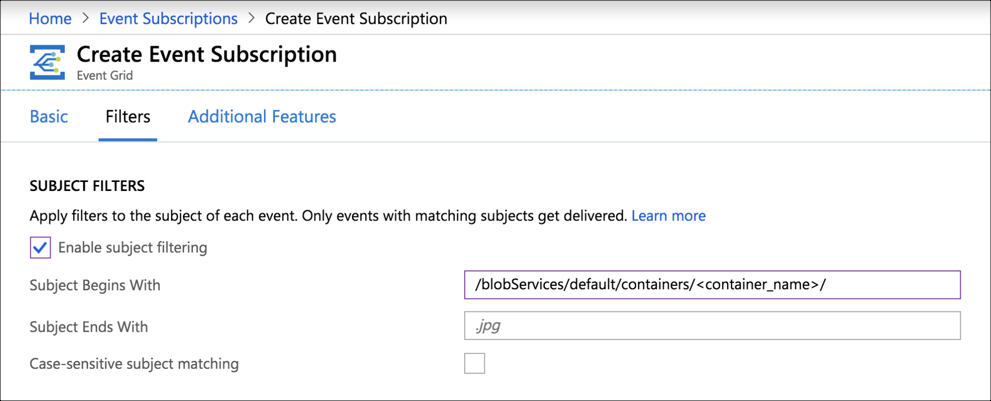
Click Create.
Verify the deployment was successful by checking Notifications in the top right corner of the Azure Portal.
Step 3: Enabling VNet Integration (Optional)
Assuming you have used the modified template which uses standard/premium plan for BlobTaskConsumer and DLQTaskConsumer functions. This assumes that your storage account access is enabled for selected networks.
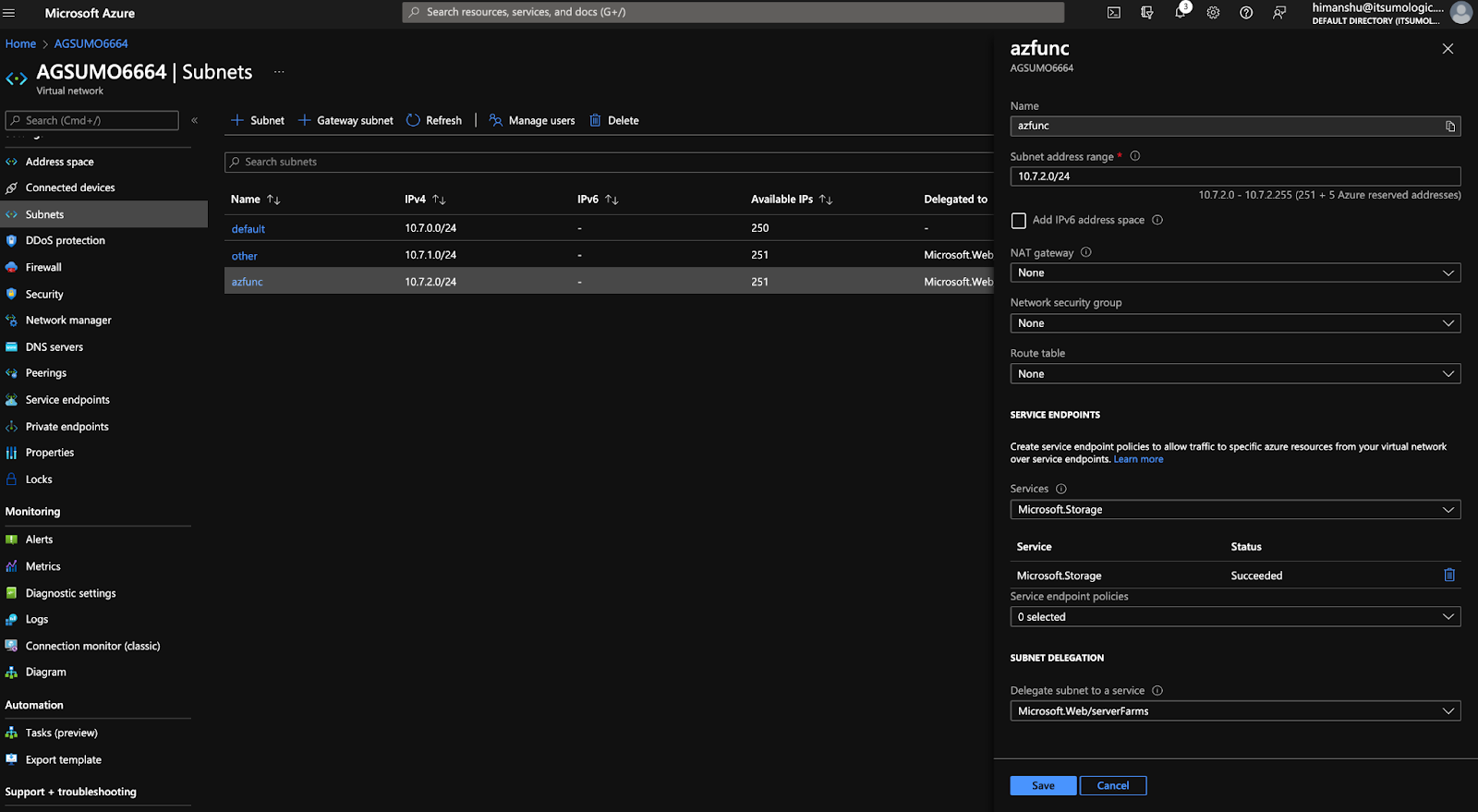
Create a subnet in a virtual network using the instructions in the doc. If you have multiple accounts in the same region you can skip step 2 below and use the same subnet and add it to the storage account as mentioned in step 3.
Perform below steps for both BlobTaskConsumer and DLQTaskConsumer function apps.
Go to Function App > Networking.
Under Outbound traffic, click on Vnet Integration.
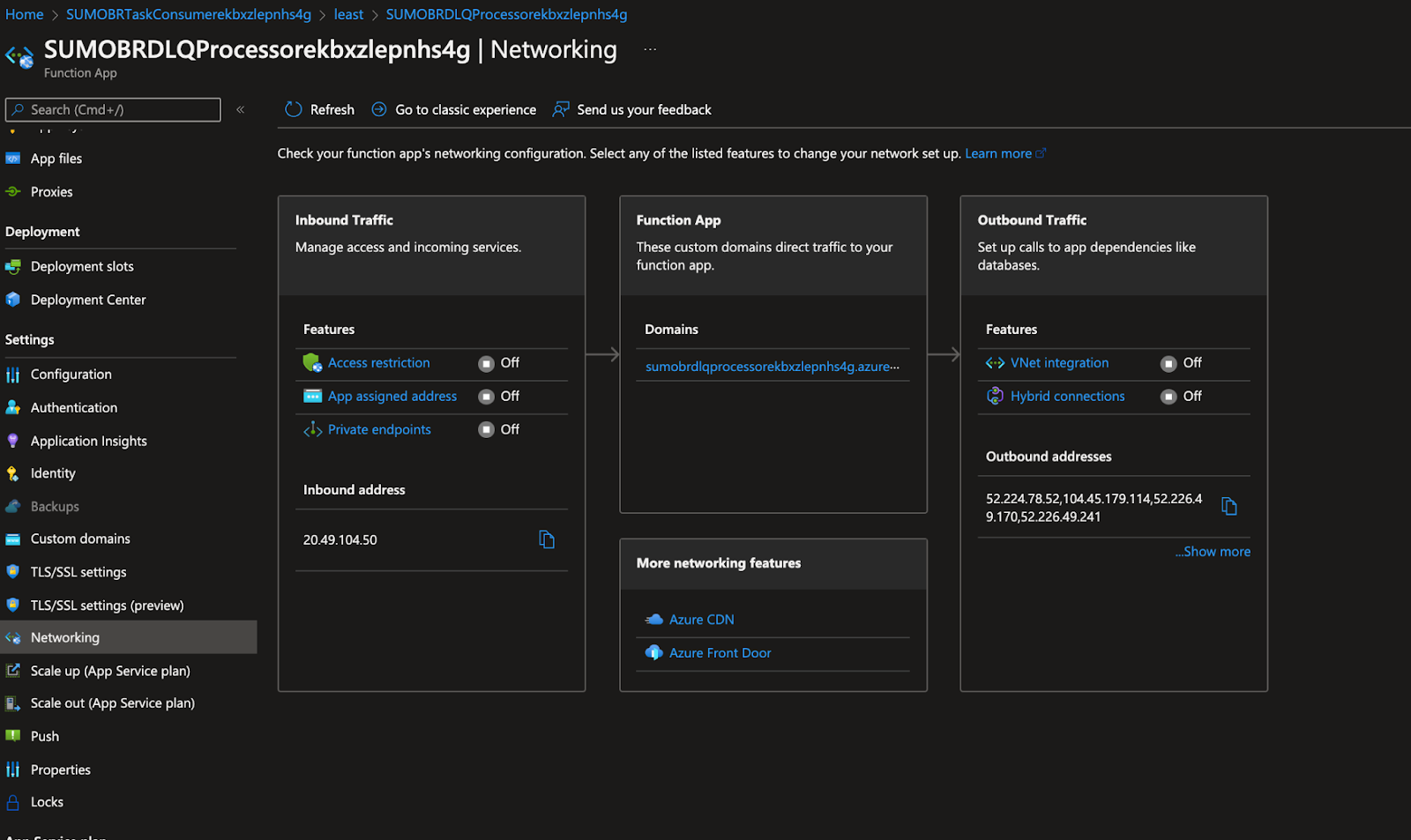
Add the Vnet and subnet created in Step 1.
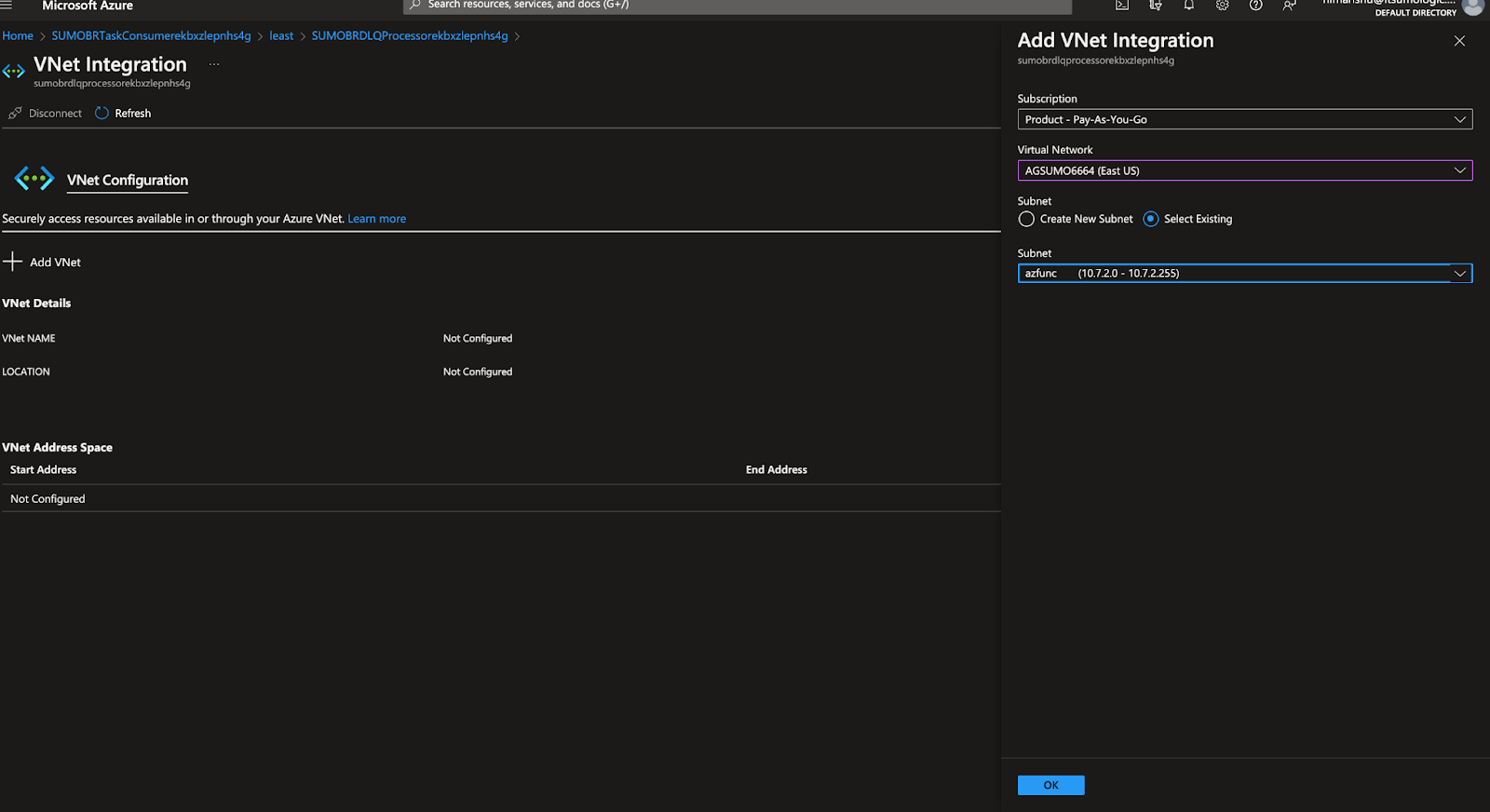
Also copy the outbound ip addresses you’ll need to add it in firewall configuration of your storage account.
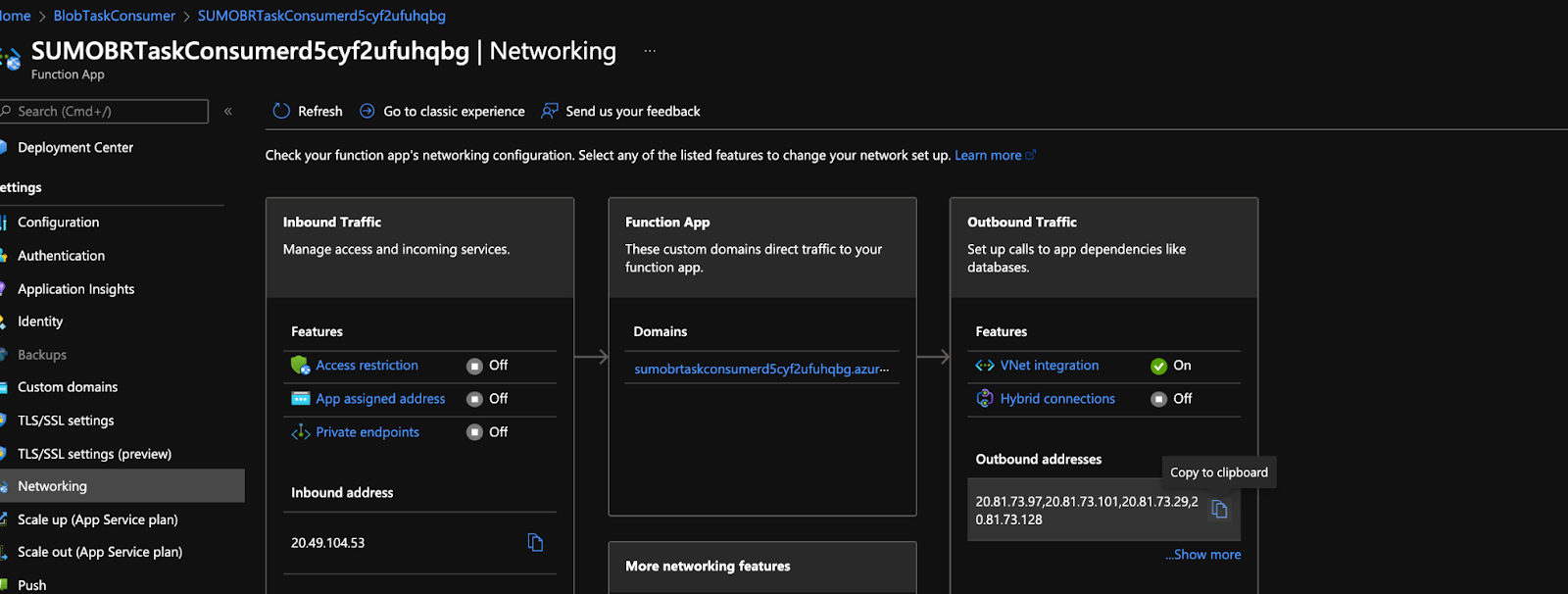
Go to your storage account from where you want to collect logs from. Go to Networking and add the same Vnet and subnet.
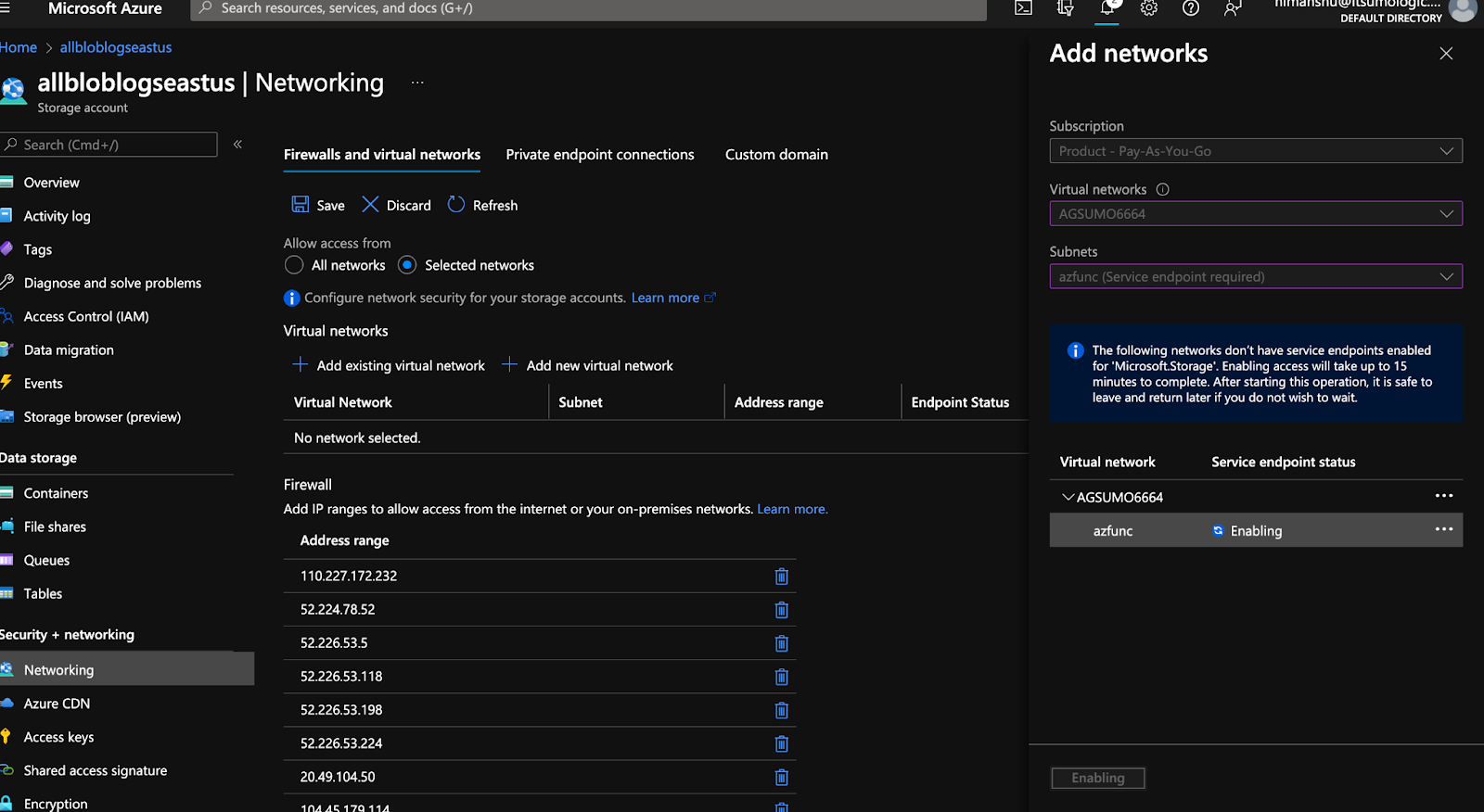
Add the outbound ip addresses (copied in step 2.d) from both BlobTaskConsumer and DLQTaskConsumer functions under Firewall with each ip in a single row of Address range column.
Verify by going to the subnet. You should see Subnet delegation and service endpoints as shown in the screenshot below.